i remember hearing, and trying to decode a "voice inversion" system that was used for ship-to-shore telephone calls from the mid 1970s to the early 1990s. a standard "voice inversion" system takes the audio as one input, and an oscillator (usually about 3khz) and input the two signals into an analog multiplier. the output of the multiplier is a double sideband signal which is then fed into a low pass filter, so only the lower sideband signal is present at the output. the lower sideband is "inverted" in the frequency domain, with low frequencies translated into high frequencies, and high frequencies translated to low frequencies. there was an additional trick used in the ship-to-shore telephone system (because theoretically one could set their receiver to LSB and listen in), and that was to use an envelope follower to shift the oscillator frequency. this means that the audio signal was half wave rectified, and the resulting DC voltage was applied to the oscillator to wobble it's output frequency. with the analog systems in use, there was a tiny amount of bleed-through of the oscillator, and it wasn't difficult to figure out that the oscillator rested at 3khz, and would go up in frequency when somebody was talking, and would wobble with the amplitude of the audio (or the tone was there as a "pilot" tone, and a phase locked loop would produce the local frequency modulated "carrier" signal).
here's the basic voice inversion scrambler. the input wav file is a wav file of somebody talking. the output wav file is the inverted speech. there are two greyed out wav file blocks, so that the output wav file captured on the first pass can be used on the second pass for decode (as would be done in the receiver). you can use any wav file you want as the input, but music is a bad choice. also, care must be taken to avoid clipping in the audio, because clipping will render the reconstructed audio unintelligible.
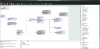
i'm currently in the process of adding the frequency modulation blocks to simulate the original ship-to-shore system.
here's the basic voice inversion scrambler. the input wav file is a wav file of somebody talking. the output wav file is the inverted speech. there are two greyed out wav file blocks, so that the output wav file captured on the first pass can be used on the second pass for decode (as would be done in the receiver). you can use any wav file you want as the input, but music is a bad choice. also, care must be taken to avoid clipping in the audio, because clipping will render the reconstructed audio unintelligible.
i'm currently in the process of adding the frequency modulation blocks to simulate the original ship-to-shore system.

